Best WAF Website Firewall Solutions
Cyber Defense Isn’t Luck — Protect Your Website 24/7 with the Right AI WAF Partner
Tired of worrying about DDoS or hacker attacks? Yuan-Jhen Informationprovides the most trusted AI-WAF solutionson the market, helping you build a truly proactive web security defense line.
What Is a WAF and Why Do You Need One?
Cyberattacks are everywhere — from data breaches and system crashes to damaged SEO rankings — often caused by unseen security vulnerabilities.
A WAF (Web Application Firewall) acts as the gatekeeper in front of your website. It sits between the user and your web server, analyzing every HTTP/HTTPS request to detect abnormal traffic, attack patterns, and suspicious commands.
Unlike traditional firewalls that only block IPs or ports, a WAF focuses on the Application Layer (Layer 7). By combining AI threat intelligence and global security data, it identifies malicious intent hidden within web requests — blocking DDoS attacks, SQL injections, XSS exploits, and more — all without affecting your site’s performance.
Think of it as an AI-powered security guard who understands your website’s logic and risks, working tirelessly 24/7 to ensure every legitimate visitor reaches you safely.

How Does a WAF Protect Your Website? What Types of Attacks Can It Block?
Behind every website, there are countless hidden attack attempts happening every second. A WAF uses AI algorithms and threat databases to detect and block attacks before they reach your server, protecting your invisible security gaps. A WAF can defend against:
DDoS (Distributed Denial of Service)
Blocks abnormal high-volume traffic that aims to crash your website.
Layer 7 Attacks
Detects and mitigates HTTP Flood or Slowloris attacks that exhaust server resources.
SQL Injection
Stops malicious queries from altering or stealing your database content.
XSS (Cross-Site Scripting)
Prevents malicious scripts from stealing user data or hijacking browsers.
Malicious Bots / Automated Scanners
Blocks unauthorized crawlers that cause overload, data leakage, or SEO drops.
Brute-Force / API Abuse
Detects and blocks automated login attempts or over-used API calls.
A modern WAF doesn’t just “block” — it understands and reacts to attacks intelligently, ensuring maximum security without disrupting real users.
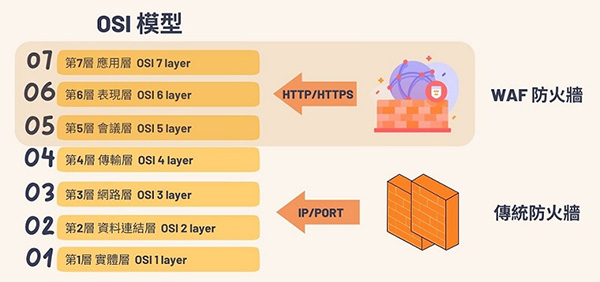
WAF vs. Traditional Firewall — What’s the Difference?
You might ask, “I already have a firewall, do I still need a WAF?” Yes — absolutely!
A traditional firewall only protects the Network Layer (Layer 3/4), managing packets, IPs, and connections. However, most modern attacks now target the Application Layer (Layer 7) — where your website logic and data live. That’s exactly where a WAF shines.
| Feature | Traditional Firewall | WAF (Web Application Firewall) |
|---|---|---|
| Protection Layer | Network / Transport (L3/L4) | Application (L7) |
| Attack Detection Accuracy | Low, IP-based filtering | High, behavioral & content analysis |
| Blocking Method | Static rules (e.g., IP blocking) | AI analysis + threat database |
| Traffic Analysis | Basic monitoring | Deep HTTP/S behavior inspection |
| Maintenance | Manual rule updates | Auto-learning + cloud updates |
| Deployment | Hardware-based, less flexible | Cloud or hybrid deployment |
| Ideal For | Internal corporate networks | All public websites, APIs, platforms |
Yuan-Jhen’s Recommended WAF Solutions|Dual-Core Protection — AI-Driven Website Security
Whether you’re a large enterprise requiring compliance-grade defense or an SME seeking fast, scalable protection, Yuan-Jhen offers two leading WAF solutions designed for every business size and security need.
AI + behavior-based detection blocks sophisticated web threats.
Powered by the CMI logic engine, Penta Security COCEP™ WAF protects high-risk sectors like government, finance, and healthcare.
- High accuracy and zero false positives
- Flexible deployment (on-premises, virtual, private cloud)
- Meets global security standards (e.g., CC Certification)
A lightweight, fully cloud-based WAF powered by AI.
No hardware required — deploy instantly and enjoy complete real-time protection against common web threats.
- Cloud deployment — start within 15 minutes
- Automatic protection against OWASP Top 10 vulnerabilities
- Blocks malicious traffic, brute-force attacks, and API abuse
Penta Security COCEP™ WAF vs. Cloudbric — Which WAF Is Right for You?
When choosing a WAF, one of the biggest questions is: “Which solution fits my needs best?” Here’s a quick comparison between Penta Security COCEP™ WAF and Cloudbric AI-WAF:
| Feature | Penta Security COCEP™ WAF | Cloudbric AI-WAF |
|---|---|---|
| Deployment | On-prem / VM / Private / Hybrid Cloud | Fully Cloud-based |
| AI Detection | Advanced CMI engine with semantic analysis & prediction | AI behavioral model for anomaly detection |
| Protection Scope | OWASP Top 10, API, Layer 7, DDoS | Common attacks: SQLi, XSS, bots |
| Accuracy | Enterprise-grade precision, ultra-low false positives | High accuracy for standard web attacks |
| Blocking Method | AI + signature-based content inspection | Cloud AI + blacklist filtering |
| Management | Best for expert teams, SIEM/SOC integration | Simple dashboard for non-technical users |
| Ideal Users | Large enterprises, finance, e-commerce | SMEs, blogs, brand sites, dev environments |
| Pricing | Based on scale; higher protection level | Subscription-based, pay by traffic |
✔ Choose Penta Security COCEP™ WAF if you’re in a regulated industry or require advanced customization.
✔ Choose Cloudbric if you need quick, affordable, and fully automated protection.
Don’t Wait Until It’s Too Late — Secure Your Website Today
Choosing the right WAF is like hiring a 24/7 intelligent bodyguard for your website — one that never sleeps, continuously blocks hackers, filters suspicious traffic, and safeguards customer data.
Recommended Security Add-Ons — Enhance WAF Protection
A WAF is your first line of defense, but combining it with other security tools creates a stronger, end-to-end protection network.
Vulnerability Scanning
Automatically detect security flaws in your website, systems, or applications before hackers do.
- Covers OWASP Top 10 vulnerabilities
- Generates detailed reports for compliance and patch tracking
SSL Certificates
Enable HTTPS encryption to protect data and boost SEO trust.
- Strengthens website security & professionalism
- Supports multiple domains and EV validation
Code Signing Certificates
Digitally sign your software, drivers, or scripts to prevent tampering or impersonation.
- Ensures code integrity and trusted origin
- Cloud-based option for easy setup
S/MIME Email Certificates
Encrypt and authenticate emails to prevent tampering or spoofing.
- Email signing, encryption, and anti-spoofing
- Protects sensitive corporate communication
Penetration Testing (PTS)
Simulate real-world cyberattacks to assess system vulnerabilities.
- Mimics actual hacker attack paths
- Customizable test levels and scope
Want complete website protection? Explore all our cybersecurity solutions in one place.
Yuan-Jhen provides 10+ cybersecurity solutions covering SSL, WAF, email protection, scanning, and more. Build a unified, multi-layered security architecture today.
→ View All Security Solutions or Call: +886-2-4499-343 or or contact us online for a free consultation!





