Cloudbric AI-WAF
Cloudbric-AI-WAF
Web Application Firewall
By continuously monitoring and filtering HTTP/HTTPS requests, it identifies malware and blocks malicious attacks. It stops suspicious traffic at the edge, ensuring only legitimate and safe traffic reaches your website. Powered by Penta Security and proudly provided by Yuan Jhen Information, Cloudbric WAF leverages continuous AI machine learning to automatically safeguard every corner of your digital presence.
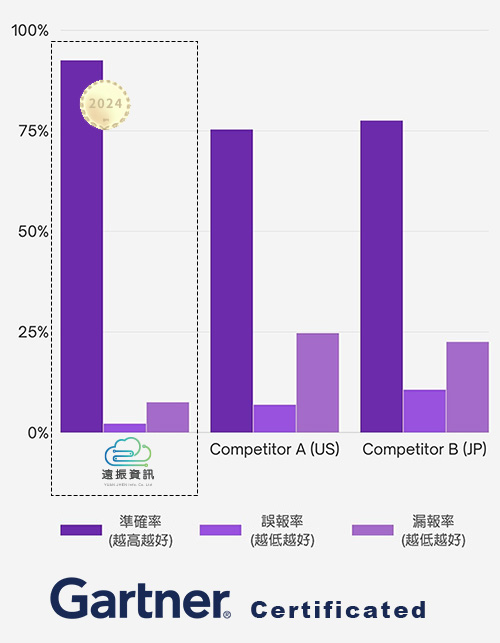
Yuan Jhen Information's Cloudbric AI-WAF is recognized by Gartner (2024) and ranked #1 in both the WAF and Cyber Attack Defense categories by Japan's leading IT review platform, IT Trend, in 2025. Choose Yuan Jhen for beyond-standard protection at the most cost-effective price.


$51.67 USD / month / domain
- * Bonus: Receive a Free DV SSL Certificate with your Cloudbric AI-WAF purchase (One per year, applicable only within the Cloudbric AI-WAF platform) — A $30.00 USD/year value.
- * A one-time setup fee of $33.33 USD applies for the initial launch. The setup fee is waived ($0) if you choose an annual billing plan.
- * This service includes 2TB of free monthly traffic. If you require more bandwidth, please fill out our contact form, and a specialist will customize a plan for you.
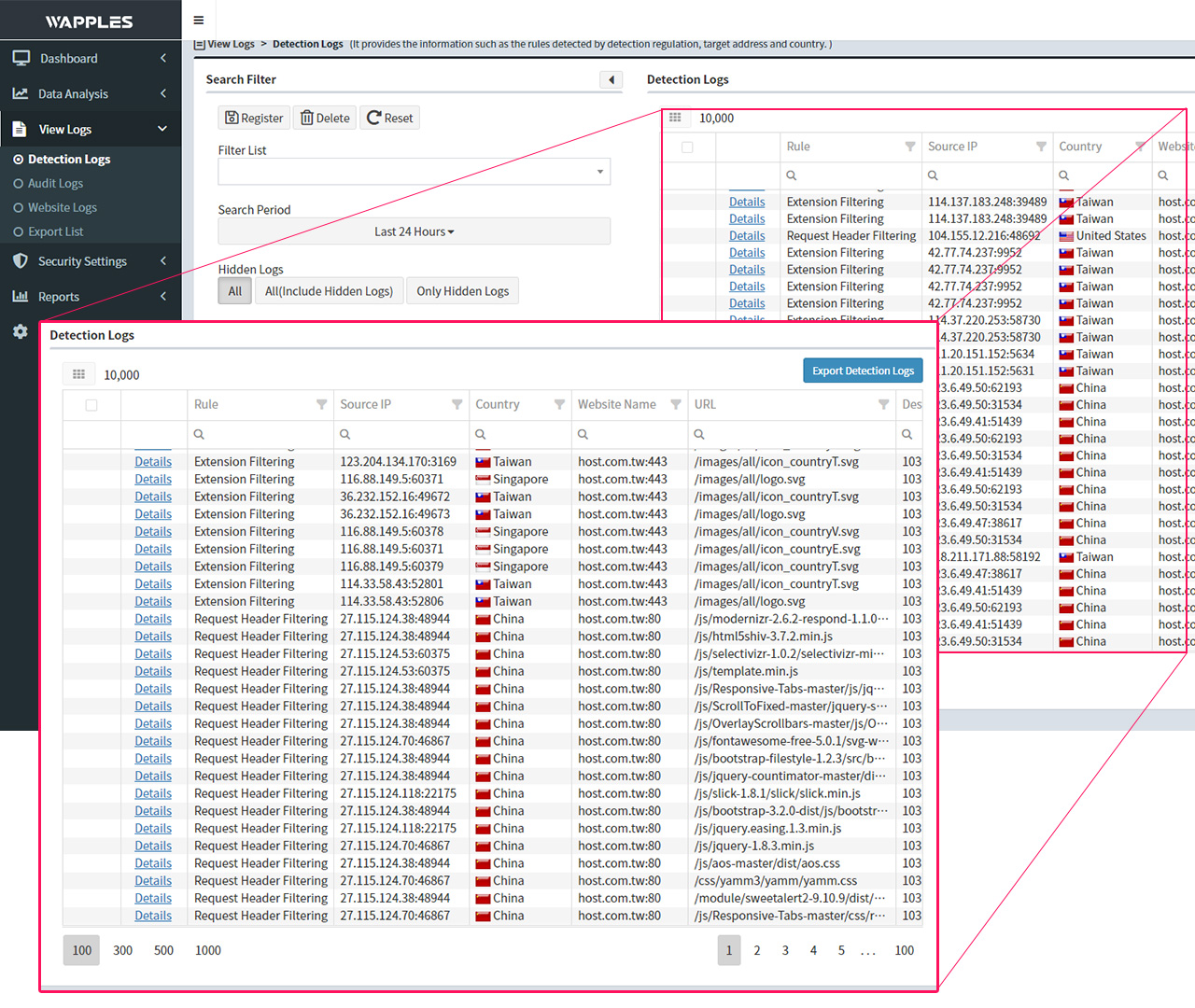
Empowering Web Security & Identifying Unknown Threats in Real-Time
- High-Precision Detection: Features a logic-based detection engine and machine learning AI modules for maximum accuracy with exceptionally low false positives.
- Customizable Rules: Fully adjustable security rules, unlike other WAFs that only offer basic on/off toggles.
- Direct Threat Intelligence: Partnered with Penta Security for continuous analysis and rule updates, instantly identifying unknown threats and new attack patterns.
- OWASP Top 10 Protection: Safeguards your website against the most critical web application security risks.
- Comprehensive Defense: Defends against both L3/L4 (Network & Transport layers) and L7 (Application layer) attacks.
- Triple-Layered Monitoring: Authentication security, traffic monitoring, and hacker attack prevention all in one network security net.
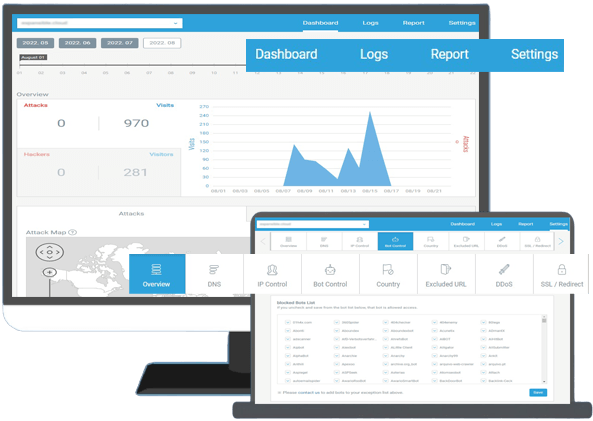
Easy Deployment, Instant Cloud Protection
- 100% Cloud-Based: No hardware or software installation required.
- Expertly Optimized: Security rules optimized by APAC's leading cybersecurity technologies and our in-house security experts.
- Quick Setup: Pre-configured security policies allow for rapid deployment.
- Taiwan Nodes: Local data centers ensure lightning-fast connection speeds.
- Visual Dashboard: Centralized dashboard displays real-time protection metrics and data at a glance.
- All-in-One Security: Includes strategy optimization, malicious traffic monitoring, and real-time reporting.
- Global Threat Sharing: Analyzes cyber threats and shares intelligence with the Cyber Threat Alliance (CTA) for real-time database updates.
Note: This plan applies to a single domain only. Subdomains require an additional purchase. A 'www' subdomain combined with the root domain is counted as one single domain.
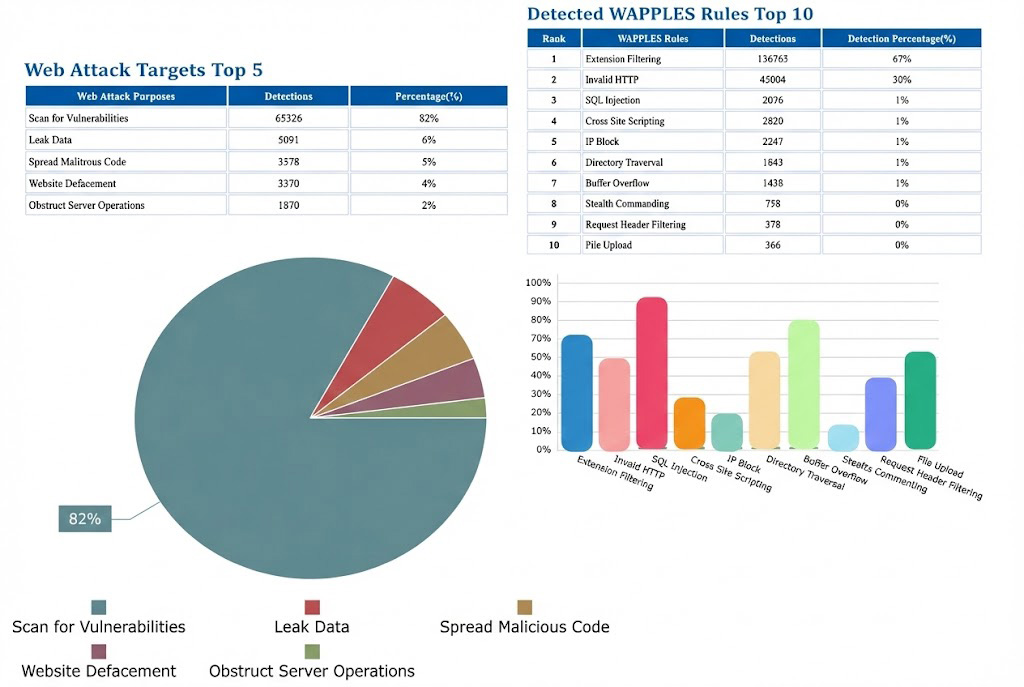
Defending Against Evolving Cyber Attacks with Cloudbric AI-WAF
As the #1 WAF in the APAC region powered by a logic-based detection engine and Artificial Intelligence (AI), Cloudbric AI-WAF effectively filters out unknown and novel malicious requests. It fortifies the security of all your web applications and systems, neutralizing Advanced Persistent Threats (APTs).
Block Cyber Hacker Attacks
Cloudbric AI-WAF instantly detects and blocks web application attacks.
Prevent Customer Data Breaches
Utilizes machine-logic algorithms for precise detection, masking confidential information to ensure data privacy.
Prevent Unauthorized Access
Detects and effectively blocks Brute-Force Attacks.
Prevent Web Defacement
Safeguards your web pages and databases from unauthorized modifications, ensuring total content integrity.
Comparison of Common Public Cloud WAF Solutions
| Comparison Item | Yuan Jhen Cloudbric AI-WAF | WordPress Plugin (e.g., Wordfence) | CDN (e.g., Cloudflare WAF) |
|---|---|---|---|
| Onboarding & Setup | Pre-launch setup handled by our professional technical team. | DIY setup. Vendor support requires an additional purchase. | DIY setup. Vendor support requires an additional purchase. |
| Rule Sets | Includes approx. 40 default Policy Sets out of the box. | Approx. 10-15 Rule Sets. (More available for purchase). | Approx. 20 Rule Sets. (More available for purchase). |
| False Positive Mitigation | Fully customizable blacklists/whitelists to significantly improve accuracy. | Mostly basic on/off toggles. Custom rules require an additional purchase. | Mostly basic on/off toggles. Custom rules require an additional purchase. |
| Pricing | $51.67 USD / month | Starts from $10.00 USD / month (Vendor support costs extra). | Starts from $20.00 USD / month (Vendor support costs extra). |
Core Security Features of Cloudbric AI-WAF
Comprehensive Defense Scope
Approximately 40 default Policy Sets defend against diverse threats, leaving no loopholes for hackers.
Unmatched Accuracy
Leverages next-generation Web AI detection for higher threat identification rates and minimized false positives.
Rapid Deployment & User-Friendly
Intuitive configurations managed through a simplified, highly secure GUI console.
Zero-Day Real-Time Protection & Auto-Updates
Direct collaboration with Penta Security ensures real-time software threat analysis and rule updates, keeping your site protected at the critical first moment!
Multi-Domain & High-Traffic Solution: Penta Security COCEP™ WAF
If you manage multiple domains or experience traffic exceeding 2TB/month, your needs require a tailored enterprise approach. Yuan Jhen Information also provides Penta Security WAF from Penta Security, the leading APAC cybersecurity brand. Penta Security WAF delivers even higher blocking accuracy than Cloudbric AI-WAF. Utilizing its proprietary COCEP™ logic-based detection engine, it analyzes the behavior and intent behind every packet in real time—without relying on signature databases or requiring lengthy machine learning periods. Comprehensively elevate your website's resilience and trustworthiness!
Fill out the form below, and our cybersecurity consultants will assist you in resolving your corporate or personal website security challenges to secure your critical customer data.
Powered by the APAC Leader in Cloud & Edge Computing Security
Founded in 1997 with a foundation in data encryption technology, Penta Security is a premier provider of network and data security products, solutions, and services. Headquartered in South Korea with a global footprint, it is the market share leader in the Asia-Pacific region. Dedicated to securing its customers through a comprehensive IT security portfolio, Penta Security is a pioneer in the APAC cybersecurity sector, having developed numerous foundational technologies. The AI-WAF stems directly from Cloudbric—APAC’s #1 WAF—equipped with advanced AI and logic-based detection engines.
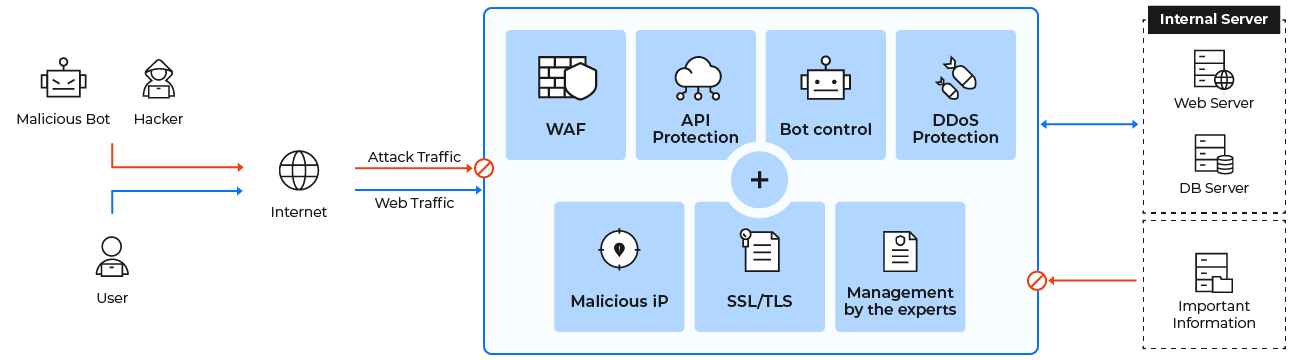
Recommended Security Add-ons
Secure Your Website Today
Choose Yuan Jhen Information's Cloudbric AI-WAF and let smart AI protection safeguard your website 24/7.
Buy Cloudbric AI-WAF Now